
Seeing to the physical security of IT hardware is more important now than ever, with the European Union’s General Data Protection Regulation (GDPR) requiring organizations to apply sound security practices to personally identifiable data from EU citizens. To get the inside story about how IT admins view the state of locking security today, Kensington commissioned a research study with Spiceworks in the United States to gather IT professionals’ perceptions about physical security risks and GDPR awareness.
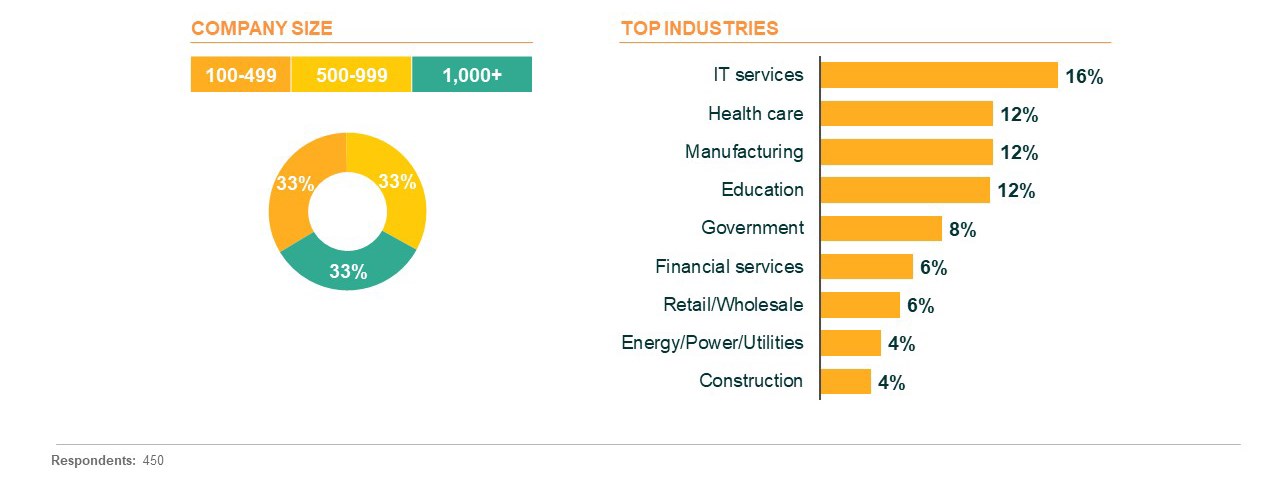
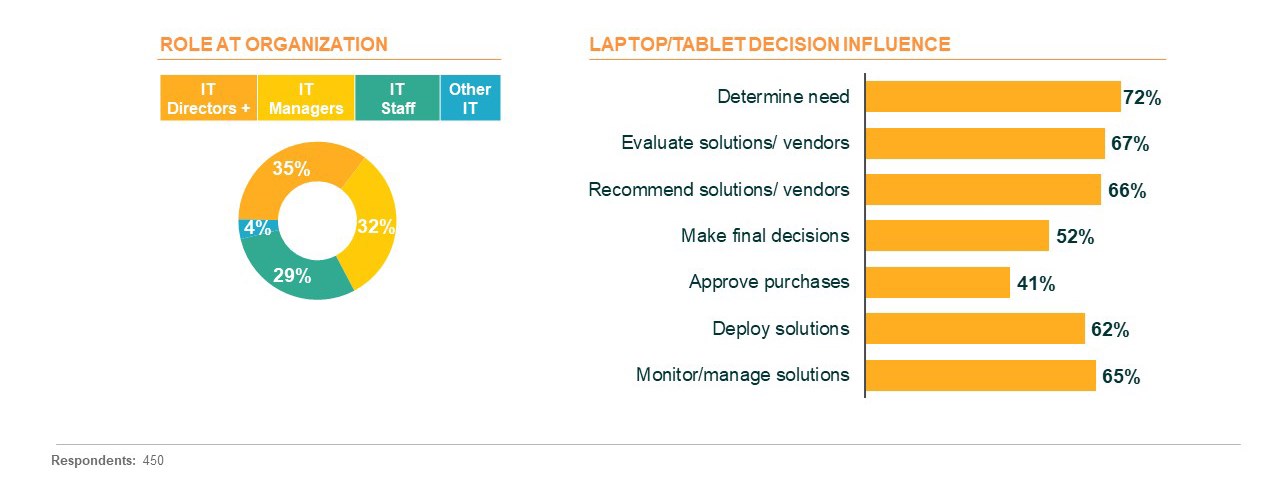
The 450 respondents who qualified to take the survey were all IT decision-makers who influenced choices about laptops and tablets at organizations with at least 100 employees. Let’s get the inside scoop on what IT admins think about current locking practices, security challenges, and GDPR implications of data loss at their organizations.
IT Pros Report High Compliance when Organizations have Security Policies
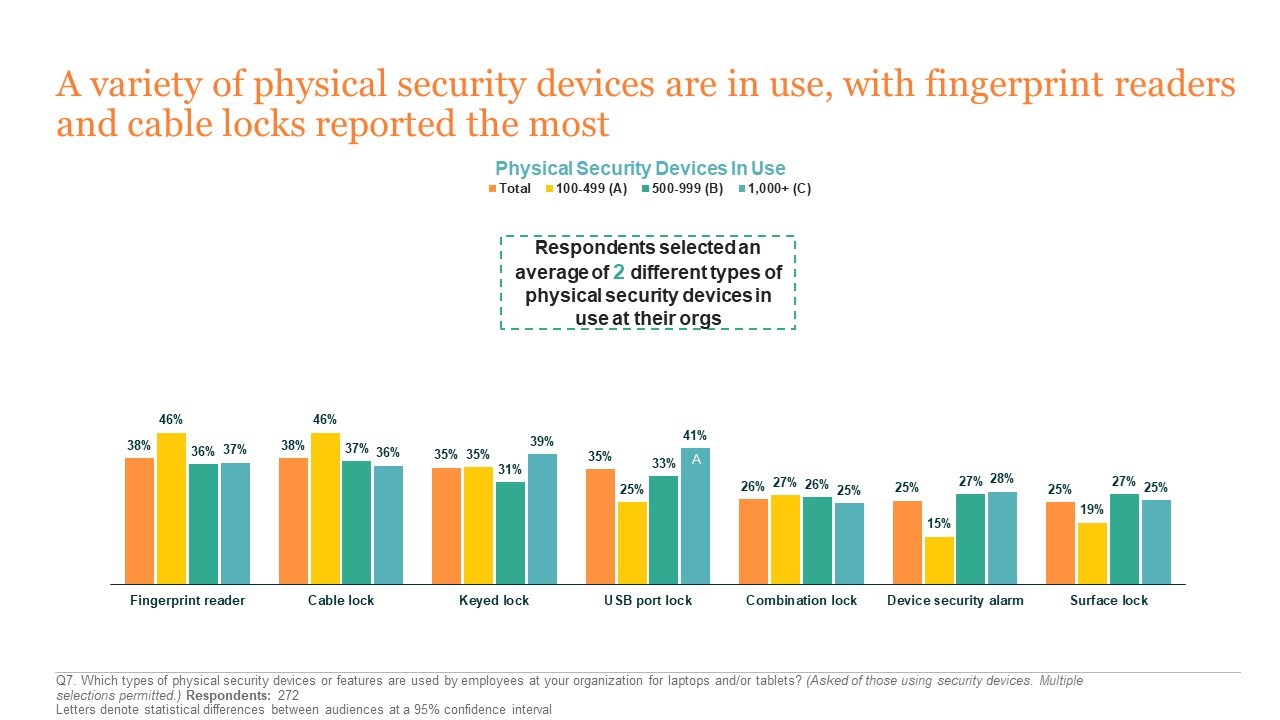
How do different organizations approach physical security today? IT admins reported that mid to large organizations are significantly more likely than smaller organizations to have a policy requiring physical security devices for both laptops and tablets. The most common physical security devices identified were fingerprint readers, cable locks, and keyed locks. While IT decision-makers reported high levels of compliance at organizations with a security device policy in place, they cite inconvenience, employee indifference and laziness, and mobility as key factors among employees that do not comply. To reduce security risks and achieve 100% compliance at organizations with a policy in place, these are clearly the challenges that must be targeted.
At organizations that do not require or recommend physical security devices, IT professionals gave several reasons for not implementing a physical security policy in the first place. A third of IT admins at organizations without a policy perceived a lack of need for physical security devices. Many indicated that their organizations had other security measures in place that they felt are sufficient, while some organizations placed responsibility for device security directly on the employees. Other IT admins reported a lack of upper management buy-in as a barrier to implementing a physical security policy.
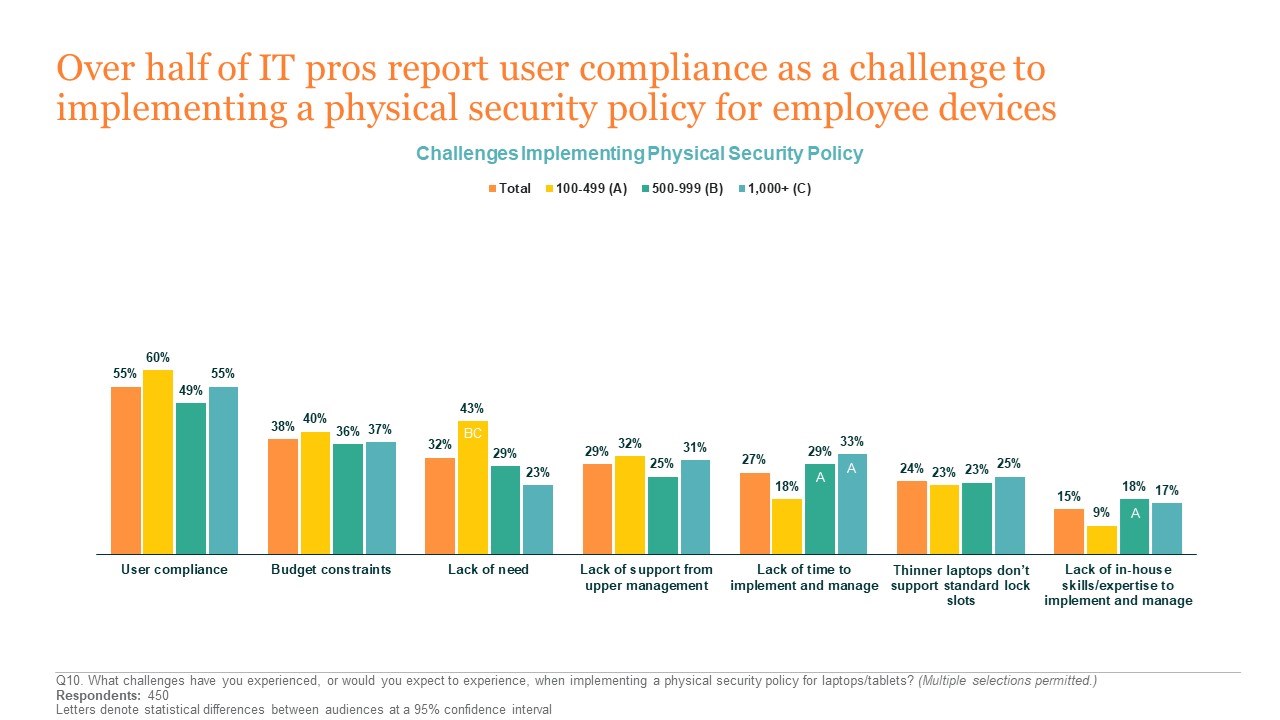
Overall, though, IT decision-makers reported that user compliance is seen as the top challenge to implementing a physical security device policy—interesting given the reported high employee compliance at organizations that have a physical security policy in place. Now that we know about current security practices at different organizations, let’s take a look at how IT professionals perceive the security risks that unlocked devices present.
Experiences and Concerns with Security Threats from Device Theft or Loss
When devices are lost or stolen, the information on those devices may be lost or compromised as well. IT professionals at organizations with more than 500 employees perceived device loss or theft and data breaches to be a higher risk than respondents at smaller organizations, and were significantly more concerned about their occurrence. Nearly two-thirds of IT admins reported experiences of employee laptops or tablets being lost or stolen, many resulting in loss of data or proprietary information.
Devices Stolen Within the Office:
“Somebody walked into the office looking very presentable, said they were going to a meeting and they knew their way, so he was let in. The person just walked around looking for unattended laptops and grabbed a few.”
Device Lost While Travelling:
“We had one of our sales representatives lose her laptop while travelling to a potential client and on her laptop was proprietary information that was vital to our company.”
Device Theft from Car:
“An employee left their computer bag in the back seat of her car and she went shopping after work. A thief broke into her car and took the entire laptop bag and contents.”
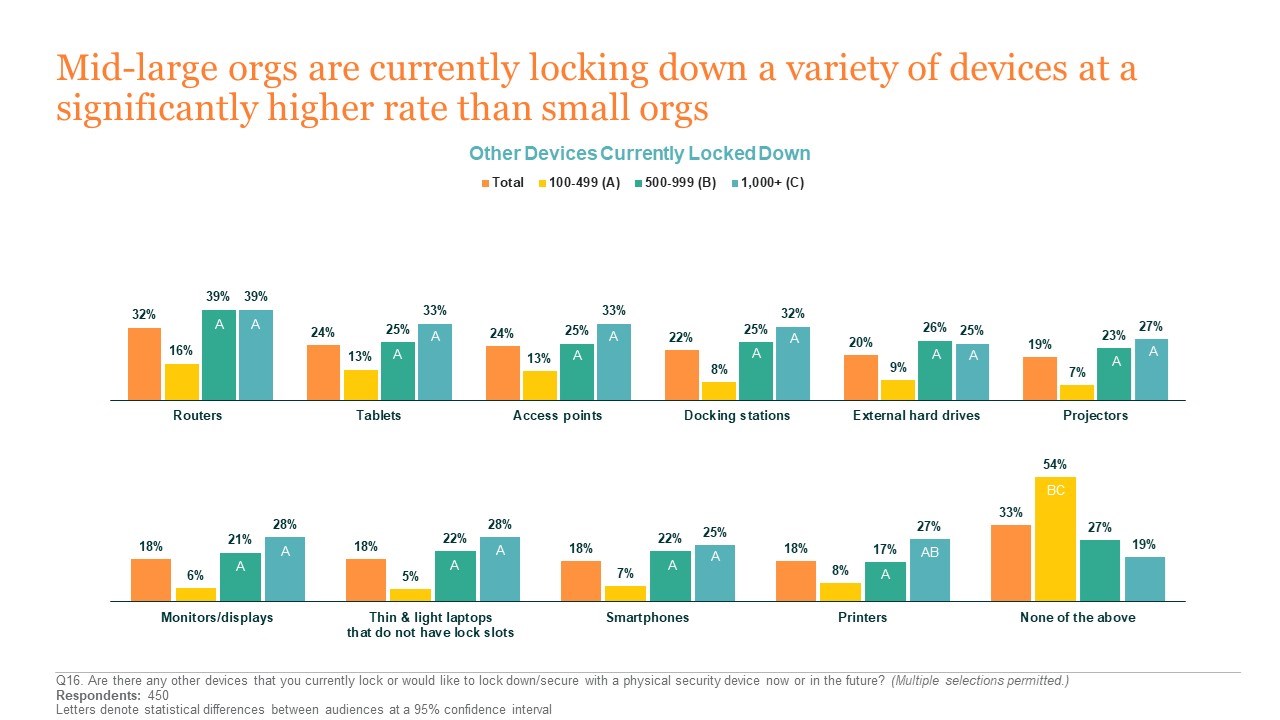
While the cost of replacing devices is a concern for many, respondents from industries that deal with large amounts of sensitive data—Energy, Finance, Government, Health Care, and Insurance—reported significantly higher levels of concern around a breach or loss of PII, potential reputation damage, and regulatory fines. Mid to large organizations are currently locking down a variety of devices at a significantly higher rate than small organizations, but IT professionals across the board cite a desire to lock down tablets and thin laptops without lock slots in the future. By keeping devices protected, locking solutions for physical security can help to protect against data loss or breach as well.
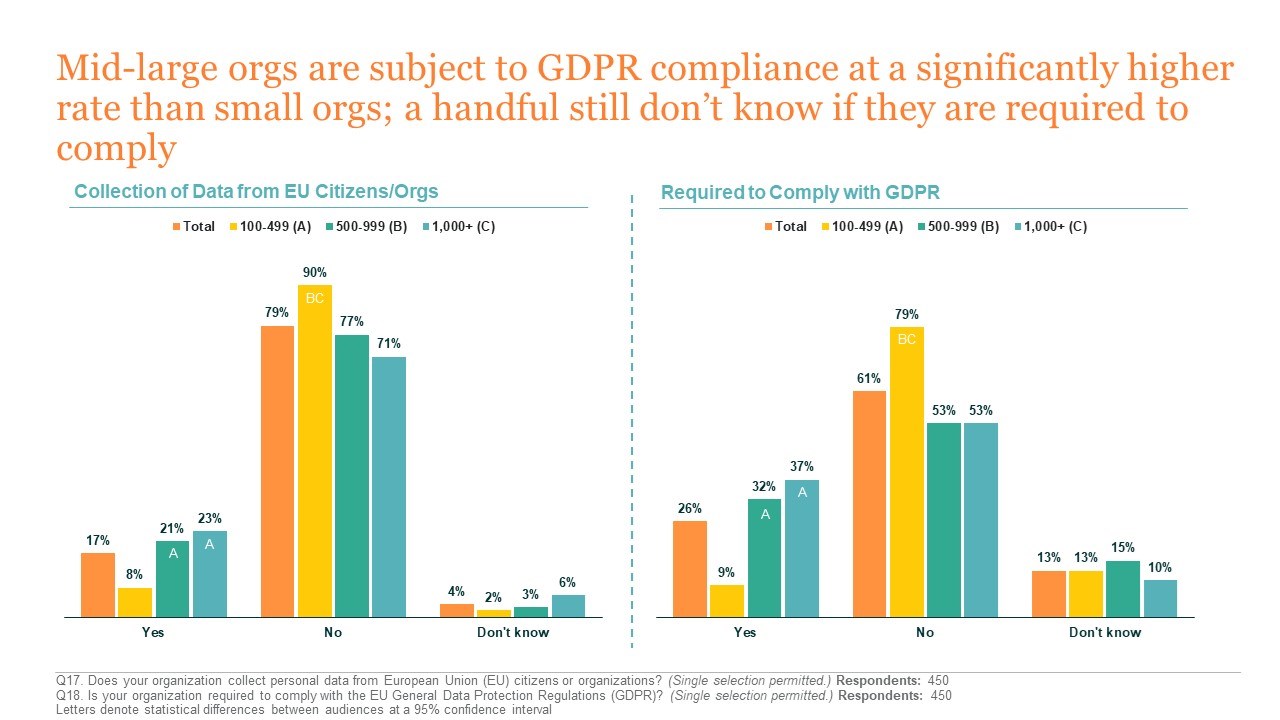
Gaps Exist in GDPR Awareness
One of the key findings of Kensington’s survey is that many organizations are still not fully aware of the implications of GDPR compliance requirements, and are not confident in their ability to comply. Less than one in five IT professionals reported that their organization collects personal data from the EU, though one in four are aware that their organization must comply with GDPR.
The survey revealed a lack of awareness around potential consequences of GDPR noncompliance. A handful of respondents stated that they do not know if they are required to comply with GDPR, and nearly half of organizations believe that failure to comply with GDPR will not have any financial implications. While mid to large organizations reported a higher level of confidence around GDPR compliance, a sizeable number of organizations—particularly those with 100-500 employees—are not highly confident in their ability to comply with GDPR.
Fortunately, IT decision-makers report they are addressing, or planning to address, GDPR at their organizations in a variety of ways, including by conducting data audits, training employees, and documenting processes to prove compliance. If you’d like more information about how to address GDPR compliance requirements, Kensington has a helpful GDPR blog that breaks down what you need to know about GDPR, its implications for data loss, and how Kensington products can help organizations apply sound security practices.
Kensington’s locking security survey gives us a better understanding of how IT professionals view the state of current physical security practices, security threats, and GDPR awareness. Learning more about how IT decision-makers are addressing physical security and GDPR standards can encourage the best locking security practices to protect our devices and the data they contain. View our full portfolio of locking and security solutions to learn more about how Kensington products can provide your organization with the most effective means of physical security.
