
Over the past 40 years, Kensington has been constantly innovating to provide the best-in-class IT productivity and security products for our customers. Within that same time frame, enterprise IT departments have undergone dramatic transformations in how they protect their enterprise identities and assets. As an industry, we've learned a few vital lessons about the nature of cyberattacks. Cyberattacks are:
- Highly motivated (e.g., monetary gain)
- Highly efficient (e.g., automated exploits against many targets)
- Highly destructive (e.g., ransomware)
- Highly preventable (e.g., phishing is lazy, but it still works!)
The unfortunate reality is that many of our internet identities (i.e., personal or work accounts) have been the target of a (typically unsuccessful) cyberattack. For example, you might have received an unexpected message with a suspicious URL from a Facebook friend followed up later by a "Sorry, my account was hacked!" post. The consequences of a successful cyberattack may have significantly greater repercussions in the workplace, ranging from a small-sum wire fraud—which can be handled internally without disclosure—to a "news headline" ransomware attack that cripples IT infrastructure and completely halts business operations.
In the Facebook example, it's extremely unlikely that your friend was singled out by an attacker. It's much more likely that the attacker was attempting to compromise any number of accounts. However, if your friend is a notable celebrity, politician, or business executive, their Facebook account could be specifically targeted by a team of sophisticated attackers that decides to remain undetected and monitor communications.
The same threats exist in the enterprise world. As an IT environment increases in size and complexity, the potential paths to a successful cyberattack also increase. An adversary may attempt to compromise a multitude of high-risk identities (e.g., IT admins, Help desk, developers, HR, finance) using a variety of techniques. If they're successful in compromising an account that doesn't result in an immediate payout, they'll use their newly compromised identity to map out additional attack paths.
Understanding Zero Trust
In May 2021, the U.S. government enacted the Executive Order on Improving the Nation’s Cybersecurity (EO 14208). One of the key takeaways is the adoption of zero trust architecture: "No actor, system, network, or service operating outside or within the security perimeter is trusted. Instead, we must verify anything and everything attempting to establish access. It is a dramatic paradigm shift in philosophy of how we secure our infrastructure, networks, and data, from verify once at the perimeter to continual verification of each user, device, application, and transaction" (DOD Zero Trust Reference Architecture). The succinct catchphrase for the zero trust model is "Never trust, always verify."
The U.S. government is actively targeted on a daily basis by sophisticated adversaries for political and monetary reasons. In the interest of homeland security, the U.S. government is also extremely motivated to implement satisfactory controls to protect its identities and assets. The pressure of a remote workforce (due to a health pandemic) has forced the government to re-evaluate its existing legacy environments as it adopts readily available and mature cloud services that can dramatically increase ease of access and productivity. This scenario is common and resonates with many of our customers.
Here are some additional requirements regarding centralized single sign-on (SSO) and phishing-resistant multi-factor authentication (MFA):
- Agencies must employ an identity provider and enterprise-wide SSO service for agency users that can be integrated into applications and common platforms and must begin decommissioning other identity systems.
- Federal agencies must develop implementation plans to integrate and enforce MFA.
- Agency systems must require internal users to use a phishing-resistant method to access their accounts.
According to the Federal Zero Trust Strategy documentation, "MFA will generally protect against some common methods of gaining unauthorized account access, such as guessing weak passwords or reusing passwords obtained from a data breach. However, many approaches to multi-factor authentication will not protect against sophisticated phishing attacks, which can convincingly spoof official applications and involve dynamic interaction with users. Users can be fooled into providing a one-time code or responding to a security prompt that grants the attacker account access. These attacks can be fully automated and operate cheaply at significant scale."
In a zero trust model, it is no longer sufficient to allow your users to connect to the corporate network locally or via VPN and proceed to use single-factor authentication (e.g., username and password) to access internal applications. Since all networks are assumed untrustworthy, those legacy applications would need to be modernized (e.g., enterprise SSO and phishing-resistant MFA) regardless of the network the user is connecting from.
Another important consideration is that some of the most popular methods of MFA (e.g., one-time passcodes [OTPS] or push notifications) that our customers have deployed today are still vulnerable to sophisticated phishing attacks.
Advantages Of Biometrics and Passwordless Authentication
Despite the hesitation to adopt biometrics for traditional enterprise devices, many of us have adopted the convenience and ease of use of biometrics with our cell phones. One of the most common misconceptions about biometrics is that a bad actor could impersonate a user by reverse-engineering their fingerprint. This type of exploitation is exceptionally rare because the attacker would need:
- Physical possession of the biometric
- A biometric with a known vulnerability
As you can imagine, this scenario is orders of magnitude more difficult and cost prohibitive for an attacker—and perhaps even impossible.
Biometrics prevents an attacker from using their most efficient and remotely exploitable techniques—such as using stolen credentials from the dark web or a phishing page that harvests your credentials as well as your MFA OTP.
Additionally, most organizations use a centralized identity provider such as Azure Active Directory (AD) or Okta for their SSO and can leverage their biometric security keys across all their federated websites. In the illustration below, Azure AD is the identity provider and Azure AD users can leverage a FIDO2 security key (e.g., VeriMark Guard) or a Windows Hello-compatible biometric security devices (e.g., VeriMark, VeriMark IT, VeriMark Desktop) to authenticate to federated applications.
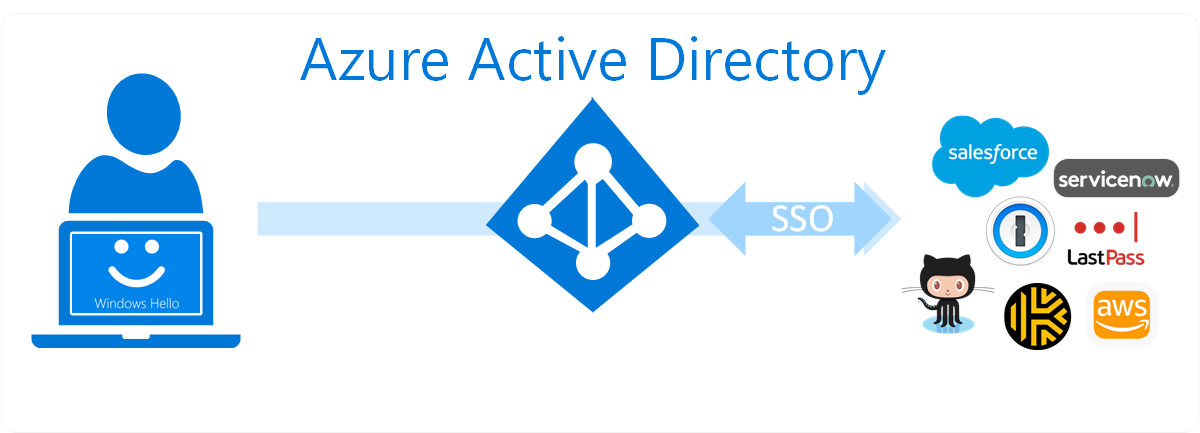
Although we can solve many of your biometric and passwordless requirements, we recognize that passwords aren’t going away anytime soon. In the same way that password managers are a great way to protect the usage of vulnerable passwords, biometric security devices are a great way to protect the usage of those password managers.
“Despite the hype, passwords just aren’t going away. . . . The use cases which utilize FIDO2 linked to password-based logins combined with two-factor authentication provide the optimal balance of usability and security. We are excited about the future of authentication and look forward to the continuing evolution of FIDO2, biometrics and multi-factor authentication.” —Craig Lurey, CTO & Co-Founder, Keeper Security
How To Protect Your Environment with Kensington
At Kensington, we’ve introduced a line of world-class biometric security products that provide substantially higher assurance for regular consumers and enterprise customers. Our VeriMark product family is built on SentryPoint, an industry-leading suite of security features for Synaptics’ fingerprint sensor that incorporates several key market differentiators, summarized in the following table.
| Synaptics SentryPoint Security Feature | Description |
|---|---|
| SecureLink | Enables strong TLS 1.2 (communication channel encryption) / AES-256 (data encryption) all the way from the sensor to the host |
| PurePrint anti-spoof technology | Detects real fingers and fake fingers |
| Match-in-Sensor | The fingerprint template is securely matched on the fingerprint sensor silicon, which limits data transfer to the host by providing a simple yes/no communication; the match result is also encrypted |
| Quantum Matcher | Accelerated matcher algorithm |
| False Acceptance Rate (FAR) False Rejection Rate (FRR) |
Synaptics SentryPoint FAR and FRR |
In the following table and screenshot, we've highlighted some of the differences between our products and their compatibility with Azure AD and Windows Hello. In addition to partnering with Microsoft to ensure that our products are compatible with their platforms, we also ensure that our products support any consumer service or enterprise identity provider that offers FIDO* authentication.
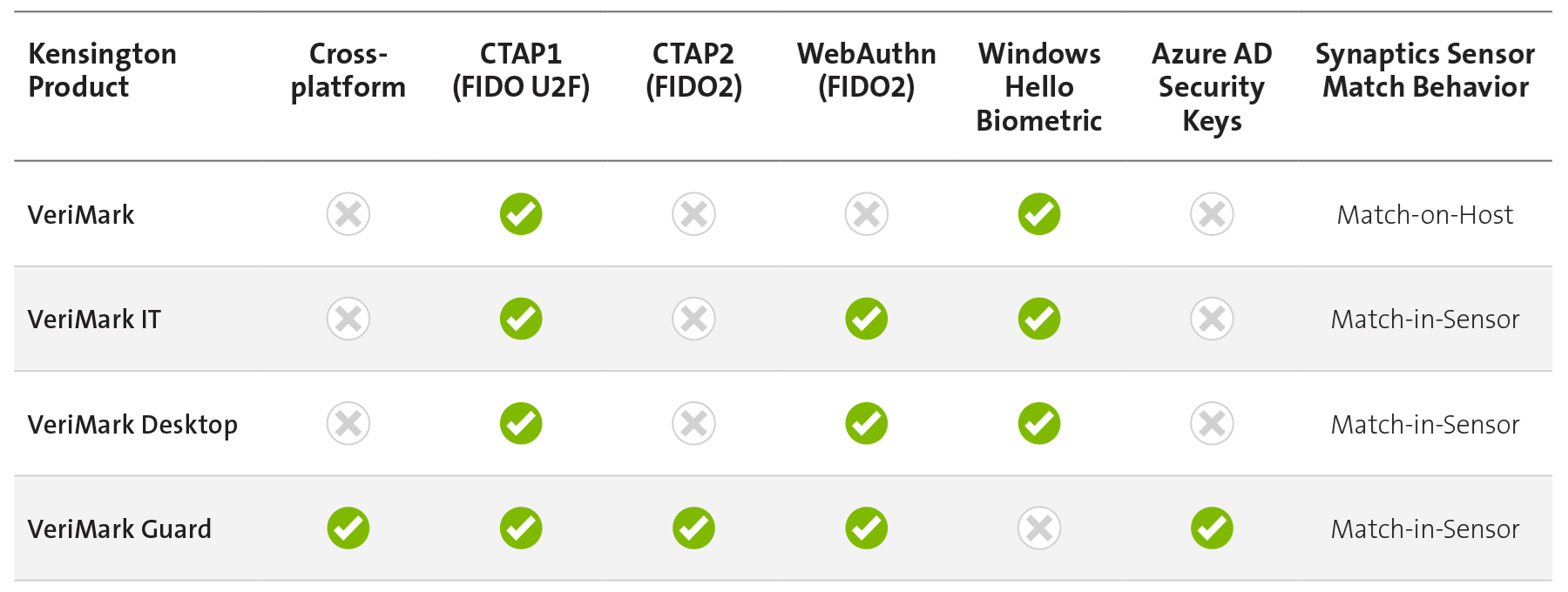
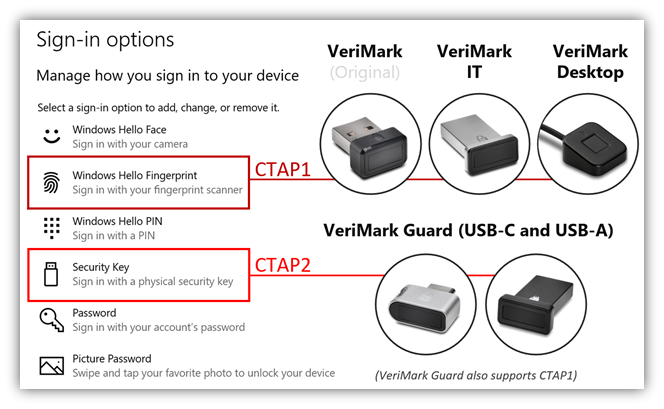
We recognize the difficulties our customers experience in determining the appropriate security tools for their environment across their many use cases. To provide some clarity, we offer the following examples:
On-site office workers
In contrast to the recent push for "working from home," many businesses simply can't support a remote workforce given the nature of their work. This may be because they are a highly optimized call center, or due to tight regulatory requirements that are common in finance and the Defense Industrial Base (DIB).
For on-site office workers, you have the option to leverage any of our products. You may want to use VeriMark Desktop or VeriMark IT to allow employees to register a fingerprint for using Windows Hello for Business and any other FIDO U2F-supported web applications. If a user is highly mobile or accesses different workstations across different operating systems on a regular basis, they may be better suited to leverage VeriMark Guard.

Off-site remote workers
In an increasingly remote workforce, it's difficult to keep track of your personnel and the locations they are connecting from. Historically, it may have been a red flag if an employee who was based in California suddenly starts authenticating from New York, but remote workers have become accustomed to the flexibility of being able to work from anywhere. For off-site remote workers, our recommendation is effectively the same as on-site workers. Some additional considerations might be whether they are 100% remote or "hybrid" (coming back to the office at some point) and whether they'll be expected to juggle between different devices, in which case the portability of VeriMark Guard might be preferable.

Shared workstations (kiosks, time clocks, etc.)
Although we often focus on "knowledge workers" when we implement new security within our organization, many businesses rely on shared workstations that are both business critical and prone to exploitation. Common examples might be a time clock or point-of-sale system. Consider the scenario in which Employee A clocks in Employee B as a favor to avoid being late to a shift—which is preventable.
VeriMark Desktop is probably the best candidate for shared workstations, especially if the workstation is being used only briefly for a quick operation before being available for the next user. You can also leverage VeriMark Guard if you want employees to be responsible for bringing their individual security keys to their kiosk; however, VeriMark Guard is a better solution if the workstation is being used for some duration of time.

Looking Forward
One of the few silver linings of the 2020-2021 health pandemic is that it encouraged organizations to rapidly modernize their applications and adopt MFA to support their growing remote workforce. Failing to adapt to the world's evolving cybersecurity threats may result in a cyberattack that could be potentially catastrophic to your organization's business or mission.
If you're ready to harden your enterprise IT infrastructure but are unsure of the best way to protect your users, our team is here to help. Contact us today!