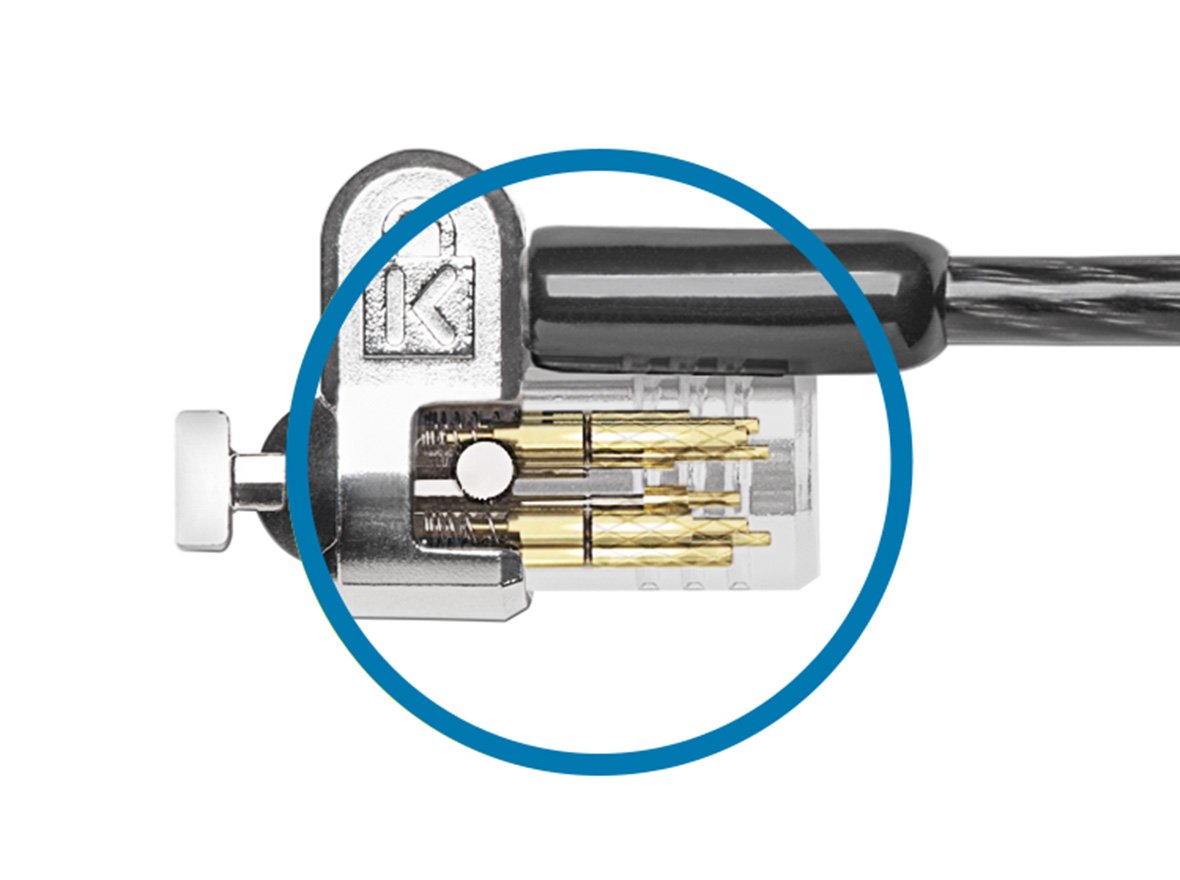
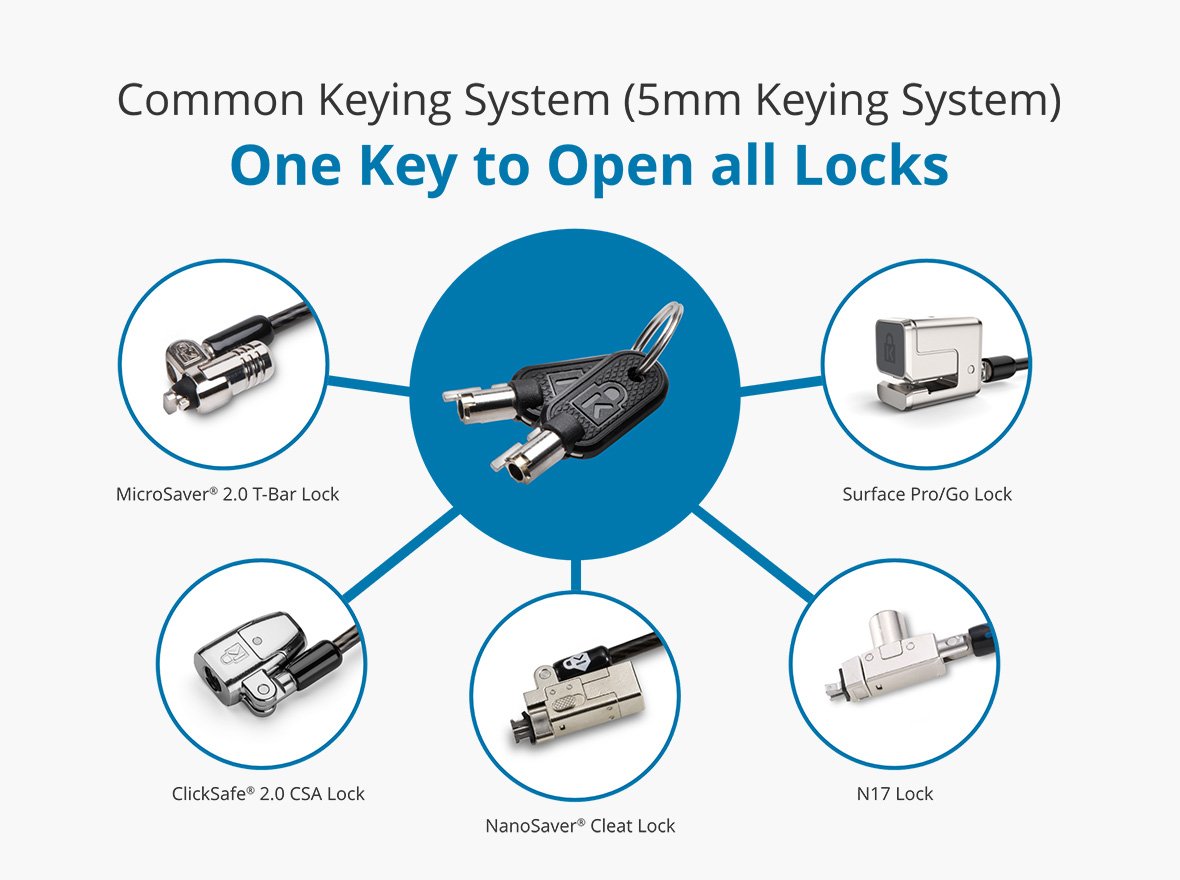
Preset Code
Serialized locks are supplied with a serial number etched on to the lock head that can correlate back to a preset code that is supplied at the time of purchase. Preset codes eliminate the need for individual users to set their combination and makes it easy to manage for IT managers.